Deep Dive into the Dark Web – Beyond the Myths
Before we dive in, this is the first part of a 7-part series on the Dark Web. In this series, we’ll explore what the Dark Web is, how it works, and how to access it safely. We’ll also cover hosting a Dark Web website, setting up entry, relay, and exit nodes, exploring marketplaces and forums, and how law enforcement tracks cybercriminals. Stay tuned for the upcoming parts as we uncover the hidden world of the Dark Web.
Introduction
The Dark Web often evokes images of illicit activities, cybercrime, and secrecy. However, the reality is far more nuanced than that. To truly understand the Dark Web, we must first differentiate it from the Surface Web and the Deep Web, explore how it functions, and debunk common misconceptions.
Surface Web vs. Deep Web vs. Dark Web - Technical Differences
Surface Web
 This is the part of the internet that you see and interact with everyday and are accessible through standard search engines like Google, Bing, DuckDuckGo, Baidu, Yandex and so on. Websites here are indexed by these search providers and hence they can be found via search queries and are linked openly.
This is the part of the internet that you see and interact with everyday and are accessible through standard search engines like Google, Bing, DuckDuckGo, Baidu, Yandex and so on. Websites here are indexed by these search providers and hence they can be found via search queries and are linked openly.
Deep Web
The Deep Web consists of content that is not indexed by above discussed common search engines. This includes:
- Databases (e.g., academic research archives, intranets)
- Paywalled content (e.g., subscription-based news, journal, streaming services)
- Private networks (e.g., corporate portals, internal networks, etc)
Well many people do interact with these services although they might not know they are interacting with it. One example is Ex Libris Primo, which allows you to explore the library of your institution which can be considered part of the deep web and similarly many journal sites as well.
Dark Web
The Dark Web itself is just a small portion of the Deep Web, the Dark Web usually requires special tools like Tor (The onion Router) or I2P (Invisible Internet Project) or freenet to access. Websites here use anonymity-focused technologies and protocols to obscure both users and hosts, commonly using .onion or .i2p domains. Since the websites purposely are made to be obscure it is not possible to index all the services/sites available here. Although you can find some search engines that try to list services that are very popular or widely known in the Dark Web Community.
How Indexing Works: Why the Deep Web is Hidden
Search engines operate using web crawlers that systematically browse and index websites. Crawlers follow link from one web page to another page and to another site creating index of everything they visit and record, which later is searchable using search engine query. However, many online resources are intentionally not indexed due to:
- Restricted access (password-protected sites, government networks)
- Dynamic content (databases that generate pages on demand)
- Security concerns (sensitive or confidential information)
- Limited interlinking(crawlers follow through link to discover other pages or domains)
Since Dark Web sites intentionally use privacy enhancing technologies and have very low interlinking it is not possible to crawl and index as in the sites/services with surface web. Hence vast amounts of Deep Web and dark web services are hidden and cannot be accessed unless you know how to access them directly.
How Tor Works-Under the Hood
The tor network enables anonymous communication through a multi-layered encryption system known as onion routing. Where it sends your traffic through three random servers also known as relays.
Onion Routing and Multi-Layer Encryption
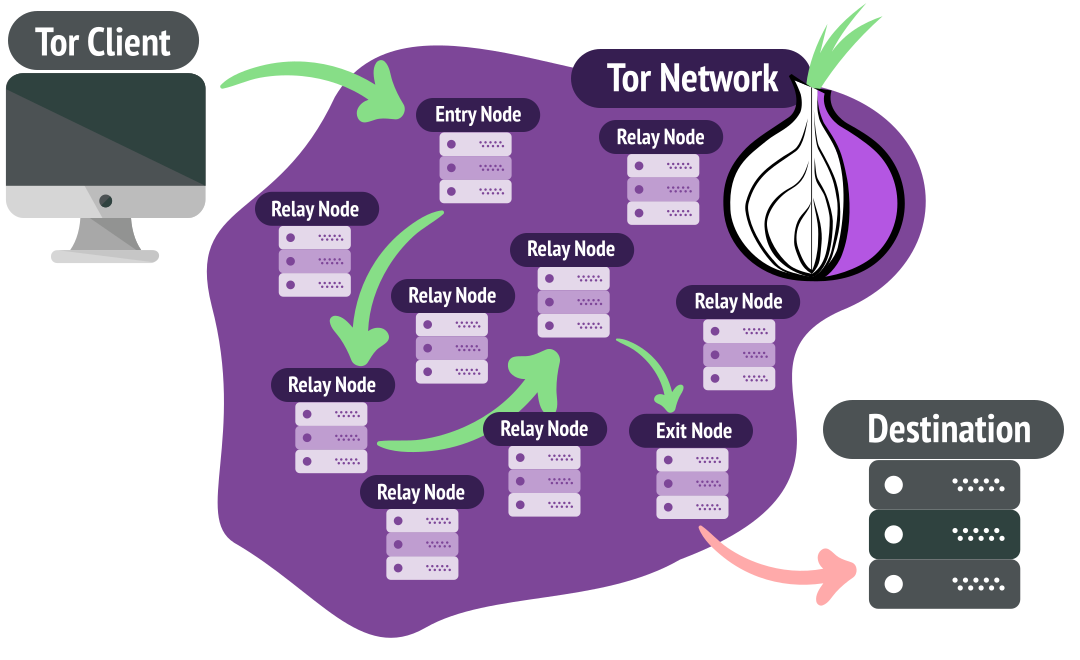 Tor routes traffic through three random volunteer operated-nodes, encrypting data at each step.The process resembles peeling an onion, where each layer represents an encrypted hop.
Tor routes traffic through three random volunteer operated-nodes, encrypting data at each step.The process resembles peeling an onion, where each layer represents an encrypted hop.
Guard Node: First node that knows the user’s IP address but not the destination. The tor client randomly selects an entry node and is persisted for a month orTor may select a new one earlier.
Middle Node: Passes encrypted traffic without knowing the original sender or final destination. The Tor network changes this with every new circuit, which typically lasts for 10 minutes by default. However, if you keep using the same connection (e.g., loading a webpage), the middle node may persist for the duration of that session.
Exit Node: Final relay the encrypts data before reaching the destination, but does not know the original sender. This also changes with every new circuit, typically every 10 minutes by default. However if connection remains active(e.g. A long file download or a persistent session), the exit node may stay the same for that session until the circuit is rebuilt. Since the exit node sees unencrypted traffic(unless end-to-end encryption like HTTPS is used), it can potentially snoop on data, but it still cannot trace back to the original sender unless additional identifying information is leaked.
Key Differences from VPNs and Proxies
VPNs, Proxies, and Tor all serve the purpose of masking the user’s IP address and providing some level of privacy, but they operate differently and offer varying degrees of security and anonymity.
VPN
A VPN (Virtual Private Network) creates an encrypted tunnel between the user’s device and a VPN server, ensuring that all internet traffic is secured. While this protects against ISP tracking and some form of surveillance, the VPN provider itself has full visibility into the user’s real IP address and traffic destinations. This means that users must trust the VPN provider to uphold their privacy and not log their activities. VPNs generally offer faster speeds than Tor and are widely used for secure browsing, remote work access, and bypassing geo-restrictions. However, if a VPN provider is compromised or keeps logs user data can be exposed.
Proxy Server
A proxy server, on the other hand, simply acts as an intermediary between the user and the destination, forwarding requests while hiding the user’s real IP address. Unlike VPNs, most proxies do not encrypt traffic, making them vulnerable to interception. Since the proxy server sees both the user’s IP and the destination website, users must trust the proxy provider not to log or misuse their data. Proxies are faster than Tor and often used for bypassing geo-blocks and content filtering. However due to lack of encryption, they offer minimal security and should not be relied on for privacy or security sensitive tasks.
Tor
Tor provides the highest level of anonymity by encrypting and routing traffic through three randomly selected relays (entry, middle, and exit nodes). Tor is highly resistant to surveillance, it also results in slower speeds compared to VPNs and proxies. Additionally, Tor exit nodes can see unencrypted traffic, which makes it important for users to use HTTPS whenever possible. Tor is best suited for anonymous browsing, bypassing censorship, and accessing the dark web, while VPNs and Proxies are more practical for general online security and privacy.
Common Misconceptions and Real-World Use Cases
The Dark Web is often portrayed as a hidden world full of illegal activity, but this is a misconception. While it does host black markets, it also serves as a critical refuge for individuals who need privacy and security. Many people , including journalists, activists, and privacy-conscious users, rely on the Dark Web to protect themselves from surveillance, censorship, and online threats. It is a space where anonymity can be used for good, not just for illicit purposes.
Who Uses the Dark Web for Legitimate Reasons?
Journalists and Whistleblowers: Investigative journalists and whistleblowers use platforms like SecureDrop to safely submit and receive sensitive information without revealing their identities and private information. In countries where press freedom is restricted, this can be a vital tool for exposing corruption and human rights abuses.
Activists in Oppressive Regimes: Many authoritarian governments censor the internet and monitor online activity, making it dangerous for activists to communicate freely. The Dark Web allows them to bypass censorship, organize protests, and spread information while remaining anonymous.
Privacy-Conscious Individuals: Everyday users concerned about mass surveillance, data tracking, and personal privacy use the Dark Web to browse securely. Some simply prefer an extra layer of anonymity when accessing the internet, avoiding intrusive tracking by governments, corporations, and hackers.
Privacy Tools Vs. Criminal Networks
The same anonymity that benefits cybercriminals also protects individuals who need secure online spaces. The Dark Web itself is neutral; it is neither inherently good nor evil. Its usage defines its morality. Just as encryption can be used both by security professionals and cyber criminals/hackers, Tor and other anonymity tools serve both legitimate users and criminals.
While illegal activities do exist, focusing only on crime ignores the essential role that the Dark Web plays in protecting freedom of speech, privacy, and security.
